Built-in Security
for Your Business Communications
We safeguard your PBX system and communications with multi-layer defense, access protection, encryption, and industry-grade privacy measures.
Product Security
Core Security Capabilities
From foundational safeguards to dynamic data encryption, P-Series enforces rigorous security policies and offers comprehensive administrative controls to help you defend against attacks, misuse, and data loss.
Compliance and Privacy
Meet Global Standards for Compliance & Data Security
At Yeastar, we take a multi-dimensional approach to put the safety of your data first. Our 3rd-party certifications and adherence to global compliance regulations speak to our commitment.
Reliable System Architecture
Enterprise-grade UCaaS Infrastructure
Yeastar UCaaS service infrastructure is built on top of AWS services with the highest level of certifications including ISO 27001 and SOC2. We understand the importance of reliability and aspire to a 99.99% uptime.
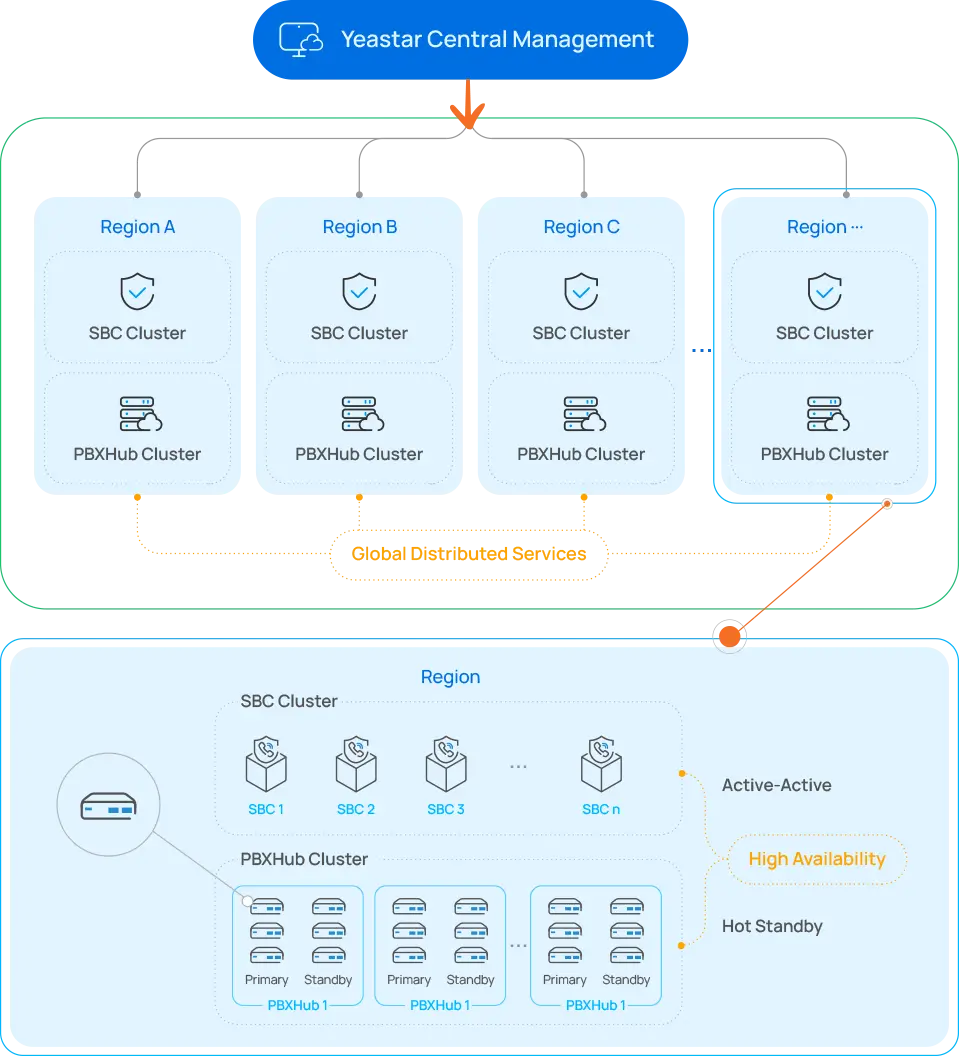
99.99% Uptime
Never miss a beat with carrier-grade severs redundant across global data centers.
N+1 High Availability
Every data center is prepared with active-active SBC high availability & load balancing.
Hot Standby Failover
Full dual-server redundancy for each PBX instance with real-time mirroring & failover.
24/7 Monitoring
Our engineers monitor the network at all times. Issues are immediately flagged and solved.
The Business Phone System You Can Trust
More Features, Greater Performance, Less IT Management
